Mobile Device Security Images

As you will not be able to retrieve your beloved photos and important contact list afterward.
Mobile device security images. That the national institute of standards and technology released its revised mobile device security guidelines during a time of increased telework is purely coincidental but also fortuitous. By shahrum gilani. Mobile security or more specifically mobile device security has become increasingly important in mobile computing of particular concern is the security of personal and business information now stored on smartphones. More and more users and businesses use smartphones to communicate but also to plan and organize their users work and also private life.
9 security gadgets for mobile devices if you use your smartphone or tablet for work you need to keep your data secure when you re on the go. Make sure that you sync your phone so your data is backed up on the cloud. Learn vocabulary terms and more with flashcards games and other study tools. Start studying mobile and device security.
Speaking of lost cell phones turn on remote tracking in your mobile device settings. Here are some solutions that can help keep your mobile devices more secure. How secure is your mobile device. If your mobile device gets lost stolen or destroyed would you feel safe that your contacts pictures apps and email data are secure.
Here are some practical steps that will help you minimize the exposure of your mobile device to digital threats. Components of mobile device security. We look at nine gadgets that try to keep your. In addition you should close open apps that you are no longer using delete app cache and limit the use of.
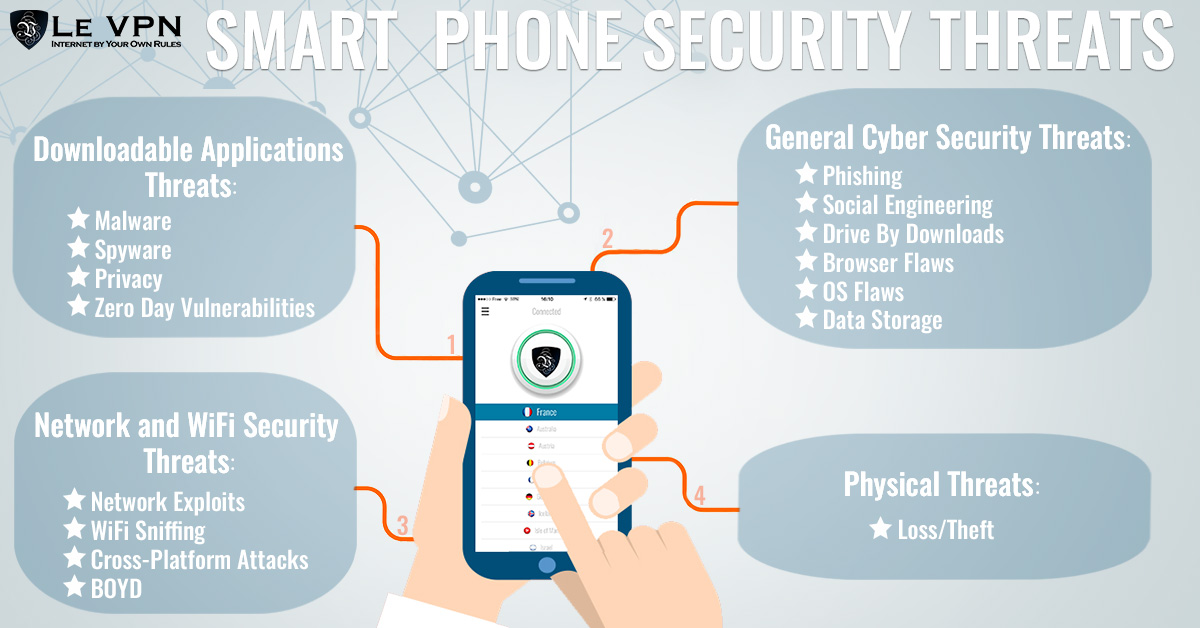
Worms and spyware unauthorized access phishing and theft. All you need to know. 914 free images of mobile device. The guidelines hadn t been updated since 2013 and much has changed across the enterprise mobile device landscape in those seven years gema howell it security engineer at.
As organizations embrace flexible and mobile workforces they must deploy networks that allow remote access endpoint security solutions protect corporations by monitoring the files and processes on every mobile device that accesses a network.