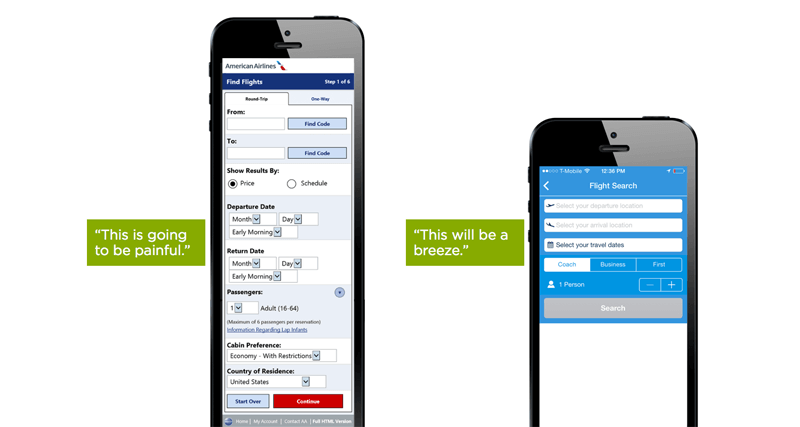
Non Mobile Devices Examples
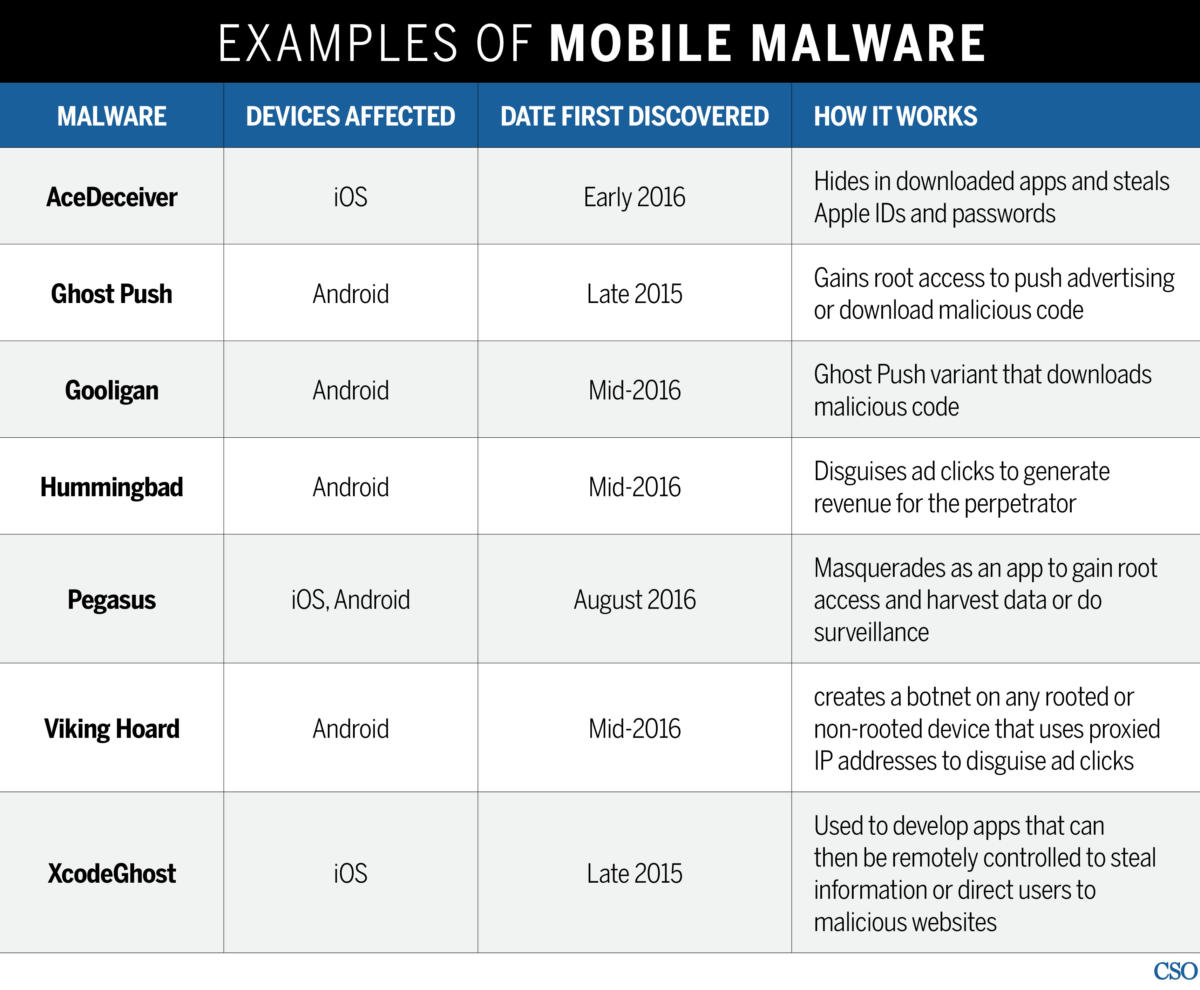
But while traditional mobile devices like smartphones and tablets may seem obvious at this point there s been a recent surge in non traditional mobile devices for field service that are.
Non mobile devices examples. For networked features that can operate over multiple channels it helps to designate a preferred channel s and design the feature for detecting the preferred channel or the next preferred channel and use that channel over others. Commonly used mobile devices include cell phones personal digital assistants pdas and multimedia players. Mobile device is a general term for any handheld computer or smartphone the term is interchangeable with handheld handheld device and handheld computer tablets e readers smartphones pdas and portable music players with smart capabilities are all mobile devices. However when it comes to identity theft in general about nine in ten mexican 91 colombian 89 and venezuelan 87 non users say they are at least somewhat concerned.
There are three basic ways mobile devices can be physically bound to mobile hosts. Accompanied surface mounted or embedded into the fabric of a host e g an embedded controller embedded in a host device. Slide 1 outline 1. Mobile device and cell phone forensics is a field of digital forensics that is growing by leaps and bounds.
In lebanon for example 3 of mobile phone non users report worries about the device being stolen and information security respectively as reasons for non ownership. For example wi fi 3g and sms are all active which is not at all an unusual situation on a mobile device. Unlike laptops desktop the resources available on mobile devices are very less like processor speed screen dimension etc. Slide 2 introduction nikolai pavlov 2005 2007 mobile qa engineer skype 2007 2008 technical pm in mobile skype 2008 2011 mobile.
These devices are quite pervasive nowadays. For nonmobile devices the execution time of classic aes ccmp and aes ccmp 256 is same and the proposed method has the same execution time as the classic method although the security is strong. The following conclusions can be drawn based on the findings of study. Another example is an autonomous vehicle.
Mobile phone data can be used as evidence in court as occurred during the recent murder trial of scott peterson and sexual assault scandal at duke university. In mobile devices using aes ccmp in rounds 8 and 9 speeds up the execution time 20 than when using round 10. Non functional testing on mobile devices nikolai pavlov.












:no_upscale()/cdn.vox-cdn.com/uploads/chorus_image/image/65392508/akrales_191001_3687_0003.0.jpg)